While Bitcoin and cryptocurrencies are often portrayed as pioneering digital money or investments, the true innovation behind these technologies lies in their ingenious application of cryptography. From secured distributed ledgers to protecting wallets and enabling trustless peer-to-peer transactions – cryptography is the fundamental building block that makes cryptocurrencies and blockchain networks possible.
In this comprehensive guide, we’ll explore the core cryptographic principles and techniques employed throughout the architecture of Bitcoin and other major cryptocurrencies. Understanding these components is essential not just for developers and engineers, but for any individual looking to truly grasp how cryptocurrencies operate and safeguard value without centralized authorities.
We’ll examine the critical role cryptography plays in areas like:
• Achieving distributed consensus across nodes
• Generating and protecting wallet keys and addresses
• Authenticating transactions on the blockchain
• Preventing double-spending and other attacks
• Preserving privacy and anonymity
By unpacking the cryptography at Bitcoin’s core, we’ll unravel why its decentralized design represents such a paradigm shift for digital cash and internet-native value transfer systems.
Hashing: A Cryptographic Lynchpin
One of the most fundamental cryptographic primitives utilized throughout cryptocurrency architecture is the hash function. Hashing refers to taking an input data of any size and mapping it to a fixed-size, scrambled output called a hash or digest.

Bitcoin and most major cryptocurrencies rely on the SHA-256 hash algorithm, which always generates a deterministic 256-bit (32 byte) output hash regardless of the input size. Even changing a single bit of the input data yields a completely different hash value. This property enables hash functions to create short digital fingerprints that uniquely identify any piece of data.
Critically, these hash functions used in cryptocurrency must be collision-resistant – meaning it should be extremely difficult to find two different input messages that produce the same output hash. This property underpins their use for virtually everything from proving data integrity to generating wallet addresses securely as we’ll explore.
In Bitcoin, hash functions are utilized at multiple core layers:
• The mining proof-of-work algorithm involves computing and comparing SHA-256 hash values.
• Transactions on the blockchain are authenticated via hash-based digital signatures.
• Wallet addresses are generated from hashes of public keys during key derivation.
• The entire blockchain is formed by chaining together blocks of data via hashing.
By combining hash functions with other cryptographic primitives like digital signatures and Merkle tree data structures, cryptocurrencies can achieve critical security and functionality requirements from an all-digital trustless network.
Securing the Blockchain Through Hash Linking
At the heart of any blockchain architecture is the hash-linked chain of blocks that permanently records all transactions on an immutable, tamper-evident ledger.
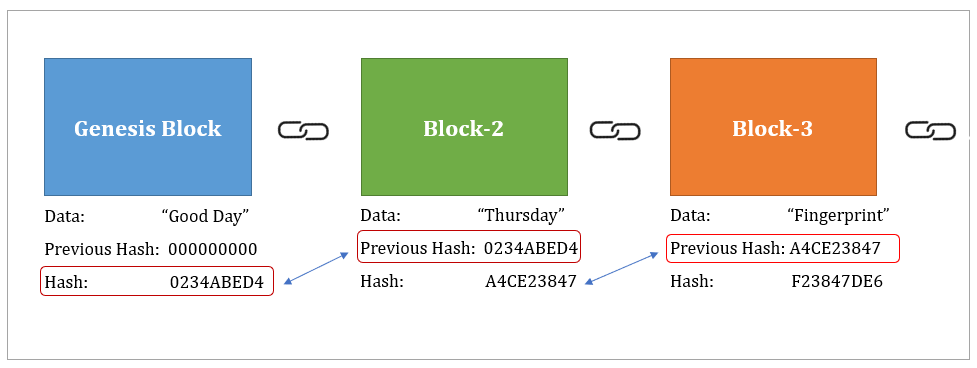
Here’s a simplified explanation of how blocks are hashed into the Bitcoin blockchain:
1) All transaction data for a given time period is bundled into a candidate block, which includes a reference to the previous block’s hash.
2) In its hunt for a valid proof-of-work solution, miners perform repeated SHA-256 hashing on the candidate block header combined with different nonce values until the output hash meets specific target difficulty criteria.
3) Once a miner solves this intensive computational puzzle, their validated block gets timestamped and linked to the main chain by including the hash of the previous block.
4) All subsequent blocks reinforce this immutable data trail, as they too must include a reference to the chain of parent block hashes before them.
The use of hash linking combined with proof-of-work establishes an immutable timeline of transactions without any central authority. Any attempts to modify data retroactively would require re-computing all subsequent blocks – an enormously difficult feat that protects the distributed ledger’s integrity.
But hashing’s utility extends far beyond just blockchain data structures. It also underpins the fundamental mechanism of generating cryptocurrency wallet keys and addresses in a decentralized manner without any coordination.
Public Key Cryptography and Wallet Addresses
At a high level, cryptocurrency transactions involve senders proving ownership of funds by digitally signing transactions with their private wallet keys. These keys are in turn mathematically derived from public/private key pairs at each user’s wallet address.

This public key cryptography system allows any user to generate their own Bitcoin (or other cryptocurrency) wallet independently in a trustless, peer-to-peer fashion.
Here’s a simplified explanation of how this process typically works:
1) A user’s cryptocurrency wallet generates a brand new random private key from a secure entropy source. This private key is essentially a large random number that must remain… private.
2) Using the Elliptic Curve Digital Signature Algorithm (ECDSA), the private key is supplied to a one-way trapdoor function to derive a public key.
3) The public key then goes through another round of cryptographic hashing algorithms to derive a wallet address that can be shared publicly.
4) To receive funds to this wallet, the public wallet address is provided, while the private key remains secured by the wallet’s owner to authenticate outgoing transactions.
Notably, there is no way to derive the private key from the public address or keys. This stems from the mathematical trap door functions – allowing easy one-way computation of public elements, without any means to reverse the process. Users are the sole proprietors of their private keys.
This public/private key infrastructure secured through ECDSA signatures effectively allows anyone to participate in a cryptocurrency network in a permissionless, trustless fashion while still maintaining exclusive ownership over their funds.
But the wallet cryptography gets even more robust to thwart theft or loss of keys/funds.
Hierarchical Deterministic (HD) Wallet Structure
Even with the strong ECDSA cryptography, there are risks of private keys being compromised or lost through physical hardware issues. An extremely effective solution that adds multiple layers of security is using a hierarchical deterministic (HD) wallet structure.

In an HD wallet, the fundamental building block is a root seed – typically a 12-24 word mnemonic phrase that’s incredibly robust against brute force attacks. This root seed can deterministically derive an entire tree of private/public key pairs for receiving and spending, all spawned from the single seed.
Using the hierarchical structure, only public “receive” addresses need to be exposed externally. The corresponding private “spend” keys remain nested levels deeper, deriving from branch points along the tree originating from the root seed.
This approach vastly reduces security risks and recovery burdens. Lose a single wallet private key or have it compromised? No problem – you can simply derive a new branch and retain all other existing wallet addresses. Lose the entire physical device or wallet? As long as you have the seed words, you can fully restore and recreate the entire wallet structure seamlessly.
Importantly, the seed can also automatically derive numerous sequential wallet addresses to further obfuscate the funds trail. A new receiving address can be generated for each incoming transaction to enhance privacy.
The seed is also extremely robust against brute force cracking, as each incremental word increases the potential combination space exponentially (2048 possibilities for 12 words). This hierarchical deterministic approach secured by the seed phrase has become the industry standard for all major cryptocurrency wallet implementations.
Multi-Signature Security Extensions
For even tighter security over cryptocurrency funds, multi-signature schemes can be layered on top of the standard public/private key wallet architecture.
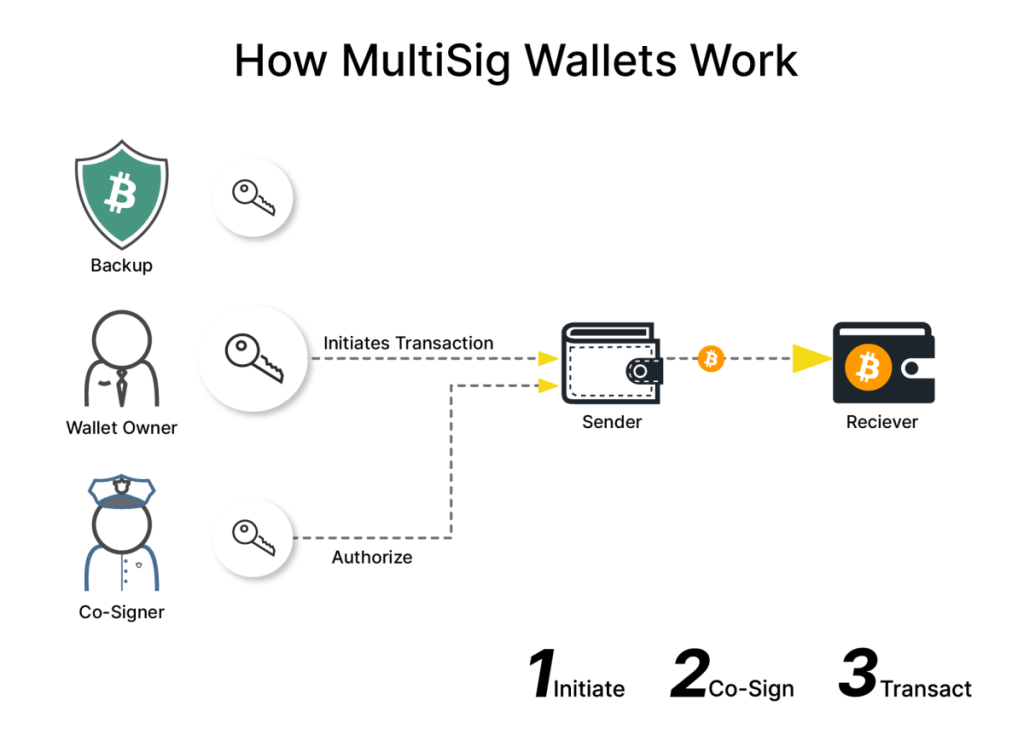
In multi-sig, a single wallet address can require a certain number (e.g. 3 out of 5) private key signatures before a spend transaction will be authenticated and committed to the blockchain. This allows creating highly secure multi-user wallets where multiple parties must consent before funds can be moved.
Multi-sig is particularly useful for cryptocurrency businesses, funds, estates and other scenarios where access to funds should require approval from multiple independent sources, rather than a single point of failure from lost/compromised keys.
The actual cryptographic implementation of multi-signature for Bitcoin and cryptocurrencies is quite intricate and incorporates components like:
• Elliptic curve Diffie-Hellman primitives for secure key exchange
• Secure multi-party computation techniques
• Complex script-based transaction validation
• More advanced Merkle tree implementations
While the details are complex, multi-sig extends the utility of cryptocurrencies far beyond simple single-signature transactions and wallets. With properly implemented multi-sig, cryptocurrency holders at any scale can build highly redundant deterrents against theft or single points of failure.
Overall, the combination of public key cryptography, hierarchical deterministic wallets and multi-signature capabilities create an incredibly robust framework for securing cryptocurrency funds in a decentralized, trustless environment unbeholden to any third parties.
Privacy, Anonymity and Advanced Cryptography in Cryptocurrencies
Beyond the core cryptographic architecture securing transactions and wallets, cryptocurrencies also employ more advanced privacy-preserving cryptographic techniques. While the public blockchain ledger is designed for transparency, there are still avenues for anonymizing user data and transaction details.
Bitcoin and most major cryptocurrencies achieve a base layer of anonymity through their public-key cryptography infrastructure. Wallet addresses derived from public keys serve as pseudonymous identities with no attached personal information by default. Users can even employ new addresses for each incoming transaction to obfuscate their payment trails.
However, the transparent nature of blockchains means that all transaction details like amounts, timestamps and paths of fund flows are publicly auditable. Sophisticated blockchain analytics firms and motivated parties can potentially map out some level of identity details through transaction graph analysis.
To achieve more robust anonymity protections, certain cryptocurrencies employ advanced privacy-preserving cryptographic methods at the base protocol and transaction levels:
Zero-Knowledge Proofs and Zk-SNARKs
Employed by privacy-centric cryptocurrencies like ZCash, zero-knowledge proofs (ZKP) allow transactions to be validated as valid without revealing any information about the amounts or wallet addresses involved.
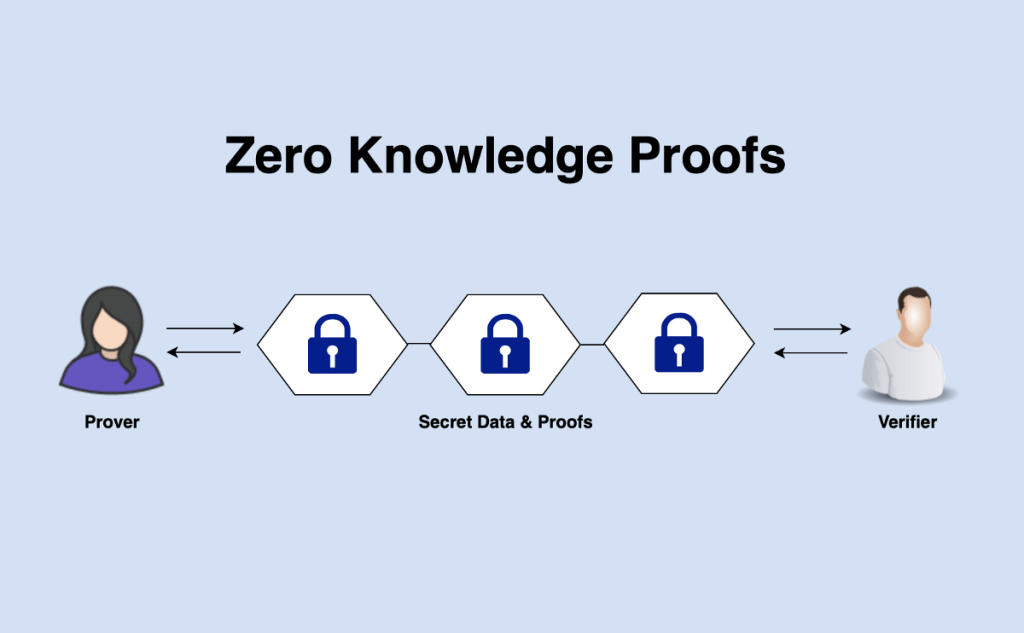
ZCash uses complex mathematical primitives called zk-SNARKs to allow transactions to be encrypted on a separate “shielded” blockchain pool while still allowing public auditing that no double-spending or counterfeiting occurred. Only the verified transaction details are committed to the public blockchain.
ZKP cryptography effectively enables a trustless, publicly-auditable ledger to preserve user privacy without any centralized coordination or “mixing” services. It’s considered one of the most advanced privacyprotocol implementations in blockchain yet.
Ring Signatures and Stealth Addresses
Other cryptocurrencies like Monero, on the other hand, employ techniques like ring signatures and stealth addresses to anonymize user identities and transactions.
A ring signature allows a Monero user to mix their transaction’s digital signature with a “ring” of multiple other signatures, preventing anyone from linking a specific transaction to a confirmed user address.
Recipients can also generate random one-time “Stealth Addresses” to receive funds, rather than a single static public wallet address that could accrue transaction history over time and be potentially traced back to the owner.
Encrypted Peer-to-Peer Networks
To further cloak user IPs and transaction data, cryptocurrencies like Monero actually route all network traffic through an encrypted peer-to-peer network of nodes not dissimilar from something like Tor. I2P, dandelion and other network-level anonymity tactics are utilized to prevent passive observer monitoring of transaction broadcasts and accompanying metadata leaks.
The end result of employing these advanced cryptographic privacy techniques like zero-knowledge proofs, ring signatures, stealth addresses and encrypted network routing, is achieving a truly anonymous, untraceable fungible currency – a feature highly valued by certain user groups.
However, privacy/anonymity also introduces challenges in supporting compliance, anti-money laundering and government oversight – which is why most major cryptocurrencies have opted for a degree of transparency rather than full-fledged anonymity networks.
Challenges and Future Frontiers
While the cryptography underpinning cryptocurrency and blockchain implementations is highly robust, it’s not an immediately perfect or complete solution. There are risks, unknowns and active areas of optimization that engineers, academics and entire disciplines are advancing.
Post-Quantum Cryptography Considerations
As immensely computationally-intensive as modern encryption schemes like Elliptic Curve cryptography are, they will be vulnerable to potential quantum computing attacks. The ability for quantum machines to efficiently solve certain problems like integer factorization would render schemes like RSA encryption obsolete.
While cryptocurrency adoption on a large scale is a long way off, academics and cryptographers are already exploring post-quantum cryptographic algorithms to someday migrate public key infrastructure to quantum-resistant primitives like hash-based signatures, lattice-based cryptography and more.
Verifiable Delay Functions: Greener Consensus Mechanisms
Much criticism has been levied at Bitcoin’s proof-of-work consensus mechanism for its intensive energy requirements. While advancing more energy efficient consensus algorithms like proof-of-stake is challenging from a cryptographic perspective, cryptographers are actively exploring more sustainable alternatives.
Verifiable delay functions (VDFs) utilize novel hash functions and randomization to introduce measurable delays that can achieve distributed consensus without expending enormous electrical resources. VDFs are an area of cryptographic research with enormous implications for reducing the climate impact of blockchains if they can be implemented securely at scale.
Multi-Party Computation and Securing Decentralized Governance
Decentralized governance over blockchain protocol updates, monetary policies and other decision rights has become an increasingly important issue for major cryptocurrencies as their scope and asset bases continue growing.
Existing coins largely utilize multi-signature primitives and naive on-chain governance voting through staking/mining pools. But cryptographers are actively researching more advanced techniques from multi-party computation (MPC) to achieve more robust accountability and collective decision-making across decentralized validator networks.
MPC and related cryptographic efforts could be instrumental for maturing cryptocurrency governance models and securely managing their궼 decentralized assets at a systemic level.
Conclusion: The Transformative Power of Cryptography
While blockchain and cryptocurrency technologies are major milestones of innovation, the true unsung hero enabling this decentralization revolution has been the discipline of cryptography. Cryptocurrencies represent a milestone convergence of battle-hardened cryptographic primitives to establish trust, integrity and consensus in a fully decentralized digital environment.
From hashing algorithms to public key cryptography, zero-knowledge proofs and advanced signatures, cryptocurrencies weave an intricate cryptographic web to remove any reliance on centralized authorities and single points of failure. While not immune to emerging threats like quantum computing, their core crypto-economic incentives and resilience rooted in rigorous mathematics have demonstrated the enduring potential of blockchain to transform industries.
Critically, the underlying cryptography employed by cryptocurrencies extends far beyond just digital cash. These techniques allow anyone globally to engage in direct peer-to-peer transactions and build robust decentralized applications without intermediaries. In that vein, cryptocurrencies are just one application example of how robust cryptography realizes the dream of a trustless economy where individuals can cooperate and transact on an even playing field.
In parallel to blockchain, cryptography will surely transform fields like digital identity, decentralized cloud infrastructure, data privacy and so much more. We are merely in the early innings of a broader “cryptographic truth revolution” that will transform systems, protocols and economies as these mathematical techniques advance.
Summary: Cryptocurrencies like Bitcoin are fundamentally cryptographic protocols that utilize techniques like hashing, public key cryptography, zero-knowledge proofs and advanced signatures to enable decentralized trust and security. Core components secured by cryptography include distributed consensus on the blockchain, authentication of transactions, generation of wallet addresses and ownership of digital assets.
Cryptocurrencies combine these foundational primitives with new innovations like hierarchical deterministic wallets, multisig security and anonymity networks. Together, this suite of cryptographic techniques creates an architecture for global value transfer without centralized authorities or single points of failure.
While not perfect, cryptocurrency represents a milestone convergence of cryptography to enable decentralized digital money, but also a model for broader peer-to-peer applications and economies to flourish through similar mathematical proofs. As quantum computing and sustainability challenges emerge, cryptographers will continue advancing new techniques to harden blockchain security and usher in a decentralized future.
If you want to know more about my work or want to connect with me, reach out to me at my linked profile
Note: In order to illustrate my thought process easily, some images from internet were used.